Background
Maintaining project dependencies can be a difficult task, especially for larger projects with many dependencies. It is important to keep track of which dependencies are being used and which versions are compatible with the project. However, this can become a challenge as new versions of dependencies are released and there may be conflicts with existing code. Additionally, it can be time-consuming to resolve these conflicts and update the dependencies, which can impact the overall development timeline of the project. It is important to have a clear strategy in place for managing dependencies to avoid these issues. In this post, we will see how to use Dependabot to automatically update dependencies for project hosted in a GitHub repository.
What is Dependabot?
Dependabot is a tool that automatically detects and fixes vulnerabilities in a project's dependencies. It works by regularly checking for updates to the dependencies in a project and submitting pull requests with the updated dependencies when they are available. This can help reduce the risk of security vulnerabilities in a project and save developers time by automating the process of updating dependencies. Dependabot supports a variety of languages and package managers, including npm, pip, Maven, and Gradle.It does this by regularly checking for new versions of dependencies and alerting developers to any vulnerabilities. Dependabot supports two modes of operation: security updates and version updates.
Security updates mode: In this mode, Dependabot monitors dependencies for known vulnerabilities and submits pull requests to update to a secure version when a vulnerability is detected. This helps developers ensure that their project is using secure dependencies and reduces the risk of security breaches.
Version updates mode: In this mode, Dependabot checks for new versions of dependencies and submits pull requests to update to the latest version when it is available. This can help developers take advantage of bug fixes and performance improvements in the latest versions of dependencies.
By using Dependabot, developers can automate the process of keeping their dependencies up-to-date and secure, saving time and effort.
Enable Dependabot for GitHub repository
In order to configure Dependabot for a GitHub repository, go to the settings for the Github repository which needs to be integrated with Dependabot. Under the code security and analysis section, there are multiple configurations related to Dependabot as shown below |
We can configure alerts, Security Updates and Version Updates separately.
Alternatively, you can also configure Dependabot by adding a .github/dependabot.yml file to your repository and specifying the desired configuration in the file. For more information on this method of configuration, see the Dependabot documentation.
Configure Package ecosystem
In the dependabot.yml file we need to configure the package ecosystem. This helps Dependabot to monitor the packages for any updates to the dependencies. Within the same project it is possible that there are more than one package manager used to manage dependencies like Node Package Manager (NPM) for Node package and Maven or Gradle for Java packages used for backend processing.In the file, specify the package ecosystems that you want Dependabot to monitor under the package_ecosystems key. By configuring the package ecosystem setting for Dependabot, you can specify which package managers and package ecosystems Dependabot should monitor for updates. This can help ensure that Dependabot is monitoring the dependencies that are relevant to your project.
YouTube video demonstrating Dependabot usage
Check out this YouTube video which explains in detail how to configure the Dependabot for a GitHub repository.
Dependabot Pull Request for updated dependencies
When Dependabot detects that an update is available for a dependency in your project, it will create a pull request with the updated dependency. This pull request will contain a summary of the changes being proposed, including the current and new versions of the dependency, and a list of the files that will be modified.
It is up to the repository maintainer to review the pull request and decide whether to merge it. If the pull request is accepted, the updated dependency will be included in the project. If there are any conflicts with existing code, Dependabot will attempt to resolve them automatically, but in some cases, manual resolution may be required.
Creating pull requests for updated dependencies helps ensure that projects are using the most up-to-date and secure versions of their dependencies. It also allows for an easy way for repository maintainers to review and control changes to the dependencies in their project.
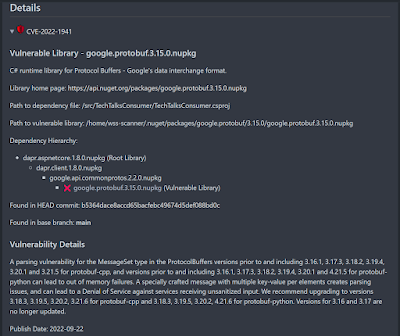
Below screenshots show different details reported in the Pull Request created by Dependabot for every dependency that is outdated in the project.
Summary of changes showing Release notes, Changelog, Commits, Compatibility issues and also commands and options.
Release notes
Advantages of using Dependabot to automatically update dependencies
Conclusion
Until next time, Code with Passion and Strive for Excellence.